Description
Synema is an application that aggregates operating system and network monitoring sensors, and that displays them in a configurable grid. It is a prototype of sysadmin monitoring tool that can be set up to monitor specific devices or general activity.
This project started as a development exercise for first-year computer science students at the ENSI of Bourges. Jean-François Lalande and Patrice Clemente from the Computer Science Laboratory of Orleans [LIFO] supervised the project and chose the sensors to be included in the application. Thirty-eight students were paired up and asked to develop a log parser for a specific sensor, or a Synema plugin that would graphically display information from the parsed log. I was, with the help of Timothée Ravier, asked to develop the overall architecture of Synema (starting with a one-week rush to provide students with a base plugin to hack). I was also in charge of assisting students in integrating their work into Synema.
It turned out that the project was too challenging for over half of the students, and few plugins made it to the integration stage. Nevertheless, the project was quite fun, and challenging for me as I had to provide an environment for total beginners to write C code. I blogged about the technical bits I’ve learnt while writing Synema at the end of the project.
Synema has been taken over by Zaina Afoulki and Aline Bousquet, leading to a publication by Aline in SECRYPT 2011. The focus in latest stages of this project has been to combine data from various sensors to visualise alerts on machines or networks. My role was to lead and coordinate development during the school project of the first year students, and I was not involved in later stages of Synema’s existence (at that time, I was working on administration tools for PIGA OS).
Is it any useful?
Synema is a research prototype, that was used by researchers at LIFO to investigate the utility of sensor correlations. But it can also be used as a teaching tool, to ask early CS students to develop code for an existing application, that fits under an already-specified API.
I have also occasionally used Synema plugins’ code to showcase how some basic static analysis tools like RATS and Splint can be used to detect security bugs. This code showcases a wide enough use of unsecure functions that it can trigger interesting conversations on the precision and usefulness of rudimentary tools like RATS. If you are interested in using/hacking Synema for any purpose, feel free to get in touch.
Media
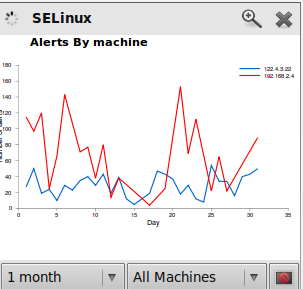
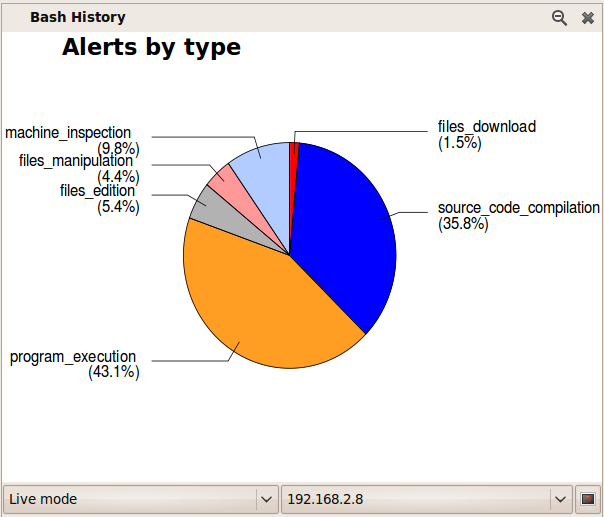
Here are some screenshots from Synema 0.5.0.1, just before I handed development over to Zaina and Aline.
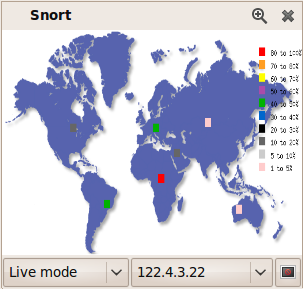
Screenshots were made later on that show the typical information to be found in charts.
Finally, two videos were released for the paper demonstration.
Where to get it
Synema’s intellectual property is shared between ENSI of Bourges and LIFO (and nobody has a clue what belongs to who), but the whole application has been written and released under GPLv3. It is available for free to download, modify and distribute (under a compatible license). Synema’s latest known released tarball is available here. Partial API documentation is also available as a tarball.
Publications
“SYNEMA: visual monitoring of network and system security sensors” Aline Bousquet, Patrice Clemente and Jean-François Lalande. In SECRYPT, International Conference on Security and Cryptography, 2011.